Modulation leakage vulnerability in continuous-variable quantum key distribution
A team of researchers from CiViQ experimentally demonstrate and theoretically analyze an information leakage vulnerability, in a continuous-variable quantum cryptographic system. They show that the final secret key may not be secure anymore if the users of that system do not properly take the leakage into account.
Realistic cryptographic systems, whether quantum or classical, are vulnerable to side channels that lead to security loopholes. In the case of practical quantum key distribution (QKD), side channels can be understood as the inadvertent leakage of information in channels accessible to a malicious eavesdropper – Eve-, who is interested in breaking the confidentiality of the messages being encrypted and exchanged by the legitimate QKD users – Alice and Bob –. Eve exploits the leaked information to obtain a significant knowledge of the secret keys obtained via the QKD protocol operated by Alice and Bob, and her ability to do this without disclosing her presence to them breaks the security assurance provided by the QKD system.
In an article published in Quantum Science and technology, CiViQ researchers from the Technical University of Denmark and Palacky University report an information leakage vulnerability that arises due to imperfections in the preparation of quantum states, or modulation, in a practical continuous-variable quantum key distribution system.
Information leakage vulnerability
Their implementation uses the so-called sideband coding approach, where information carried by the light beam is described in the form of modulation sidebands. The coherent states are prepared and measured at frequency bands shifted away from, or on a side of, the optical carrier. More precisely, the transmitter Alice encodes information about the secret key in the amplitude and phase quadrature, using optical single-sideband modulation with an in-phase and quadrature modulator. The receiver Bob decodes that information using quadrature detection using radio-frequency heterodyne measurements.
Employing in-phase and quadrature modulation and radio-frequency heterodyning, considered standard tools in the coherent optical telecommunications, for broadband continuous-variable QKD protocols use, offers the prospect of large secret key rates. This is because in an ideal optical single-sideband modulation setting, both the optical carrier and one of the two sidebands around the carrier are eliminated, effectively resulting in a single sideband at the output of the modulator. In this way, the optical single-sideband modulation and radio-frequency heterodyning potentially offer better noise performance for those systems by the placement of the desired sidebands in a manner that avoids the noisy carrier during modulation and the low-frequency noise region during detection, apart from guaranteeing spectral efficiency and immunity to dispersion.
Imperfections in the preparation of quantum states
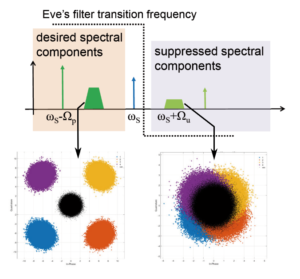
The elimination or suppression in practical optical single-sideband setups is limited, implying a leakage of the coded information via the suppressed sideband. The optical signal sent by Alice to Bob ideally consists of only the information-carrying quantum data band (dark-green trapezoid) and a pilot tone (dark-green arrow) for phase-reference alignment. Due to imperfect suppression during modulation, the same information also gets modulated in a suppressed band (light-green trapezoid) together with a suppressed pilot tone (light-green arrow), mirror-imaged across the suppressed carrier (dark-blue arrow). Eve’s attack involves filtering out and measuring the suppressed spectral components while letting the desired components go untouched to Bob. The QPSK constellation plots obtained from measurements using the desired and suppressed components show a remarkable correlation, implying that at the end of the QKD protocol Eve obtains more information about the raw key than Alice and Bob anticipate.
The obvious way to minimize the impact of this vulnerability is to maximize the sideband suppression during the process of modulation. However, due to imperfect devices, it is impossible to have infinite suppression. One way for Alice and Bob to address this security issue is to lower the bound on the secret key length, after having properly quantified the influence of the leakage, in the security analysis. In the reported work, the researchers investigated the role of trusted noise, or noise injected by Alice or Bob and not controlled by Eve, as a possible countermeasure to eavesdropping. They identified the circumstances under which injecting a controlled amount of the trusted noise can improve the security of continuous-variable QKD protocol despite poor sideband suppression. Through this work, the researchers hope to raise awareness and protect future implementations against such a vulnerability.
More information
Cited article: N. Jain, I. Derkach, H. Chin, R. Filip, U. L. Andersen, V. C. Usenko and T. Gehring. Modulation leakage vulnerability in continuous-variable quantum key distribution. Quantum Sci. Technol. 6 045001